UPDATE: April 15th, 2019. Today marks the 122nd Boston Marathon. As many of my followers know, I have ran the marathon seven times, and I look forward to it every year. My charity is The Boston’s Children Hospital, and I have raised upwards of $70,000.
Training for a marathon is a taxing, physical, emotional and expensive process. For me personally, that means five cortisone shots, almost a hundred physical therapy appointments and a few arguments with my wife. Why do it? Why climb a mountain? Why be a police officer? Why be an emergency room nurse? Why detonate a bomb in a crowd of innocent people? Not sure. We all make choices others wouldn’t and we justify our decisions based on our interests, options and perspective.

Shortly after the bombings, evacuating the city, carrying my 40lb child after running 26 miles. Hurt, angered, saddened and grateful to get to my family.
For me, I just wanted to lose weight, get fit and finally give back to a charity; killing two birds with one stone, so to speak. When you’re 50 with a young family and your health and marriage are good, bills are paid and life is settled, words like “health,” “gratitude” and “grace” begin to have more meaning. And when you become a runner, you join a special club of conscious people who understand our time is limited.
So I’ve spent the past two years raising money for Boston Children’s Hospital and disciplining myself to eat better and get in the best shape I can – I want to be of value to my family in 20 years. (Plus, “abs” has been on my bucket list.)
In 2012, there was the 86-degree heat and my awful 5:32 time, but in 2013 I was on my way to run about a 4:10 (my best time ever), but was stopped at mile 26 due to some a couple terrorists’ agenda.
During the 2013 Boston Marathon, my improved time put me on Boylston Street shortly after the blasts. There were two loud bangs, and as I rounded the corner I saw the finish line through dissipating smoke. Boston police immediately corralled runners from going any farther down Boylston because it was now a volatile area and potential crime scene. At 2:52 PM I called my wife, who was at the finish line, and got no answer. A minute later, I got my dad on the phone; he was with my wife and the kids and he confirmed they were OK. I instructed him to leave ASAP, as another bomb could go off any moment. I told him to “walk down the center of the street and avoid any cars!”
But nothing was going to keep me away from them; I couldn’t just sit there and wait. In my mind, there were bombs going off between my family and myself. As a father, son and husband, the instinctual need to get your family to safety overpowers every sense of reason. I dodged a couple of police officers and ran down Boylston, the only runner on the field, putting myself in jeopardy and now also causing law enforcement to chase after me. At the 26-mile mark, I saw people on the ground, bloody and getting medical attention from the few paramedics that were on hand to take care of runners expected to be injured in more predictable, less violent ways. I made a decision to keep going. Which still doesn’t sit well. It felt like a 3D movie where the scene was pushing me back in my chair, but the sound was off. I know the scene was loud with sirens and screams, but I heard nothing.

Then I heard an angry cop (rightly so) blasting his voice in my ear before he wrestled me off the course. Eluding further apprehension, I hopped a fence and ran down a back alley behind the restaurants, bars and shops that were evacuating people through their back doors. What I saw was people—many victims who must have made their way on their own or with the assistance of others—screaming, crying and making frantic phone calls…and there was blood. Some victims I saw lost anywhere from pints to gallons; I don’t know. I just remember not wanting to run in it.
Here is a screen shot my friend took from BAA’s website of me on Boylston running on the street then onto the sidewalk near Atlantic Fish, near mile 26 and closer to the second blast. Further down I made it into the alley.

I ended up behind the finish line and found a way to cross Boylston. I made my way to the Weston Hotel, where I found my family, scooped up my four-year-old and hiked another half mile to my vehicle. Leaving behind two vehicles, we piled nine adults and children into my Yukon and evacuated.
Out of relative danger, our attention now turned to our two children and damage control. To gauge my seven-year-old’s feelings, I calmly asked her, “Did you have fun today?” She said, “Yes, today was awesome! Until the bombs went off!” Knowing she was shaken, the radio stayed off and adults did what they could to speak in code. Note to adults who may try this: It doesn’t fool a seven-year-old.

By this time my phone was going nuts, Facebook and Twitter were buzzing and my mother, who couldn’t get in touch with us, was in complete meltdown.
Once I got home and got the kids situated, we ordered a bunch of pizza because that’s what you do when a bomb goes off. People need to feel normal.
My mom showed up at our home shortly after we got there. She was a total mess, and after the kids saw her emotional state, they understood the gravity of the situation. Today, they are showing a tremendous amount of affection and gratitude, which seems to be a side effect of their trauma.
I posted a brief note on Facebook: “Im OK, I was on Boylston St. when it happened. I saw smoke, I saw blood and people on the ground. My family was 300 yards away, waiting for me and I got to them and evacuated from the city. More later.” And the comments and “likes” poured in.
Shortly after, I provided an update: “I was right there, bomb went off. Boston police removed everyone, I kept running toward the bombs because my family was at the finish line. Police got me off the road, I resisted then another cop almost tackled me (rightly so). I ran in the back alleys, people spilling into the alleys from the explosion, screaming, crying, blood, got my dad to get my wife and kids out of there concerned for another explosion. I’m telling it to Dr. Drew on CNN between 9:15ish and 9:30ish tonight.”
Again, comments and “likes” on my page like never before. People offering an outpouring of help and support. I never knew I had that many real friends.
I feel I have to explain the part about Dr. Drew and CNN. It may seem opportunistic, but frankly, for me, it’s therapy. I do lots of media as the expert. My network is “the media.” So when I send a blast email to raise money for charity, my network knows I’m running the Boston Marathon. When I logged into Facebook and email, the requests came in from CNN, Extra and Canadian TV, along with a few radio shows too. So I spent the evening after the run as an eyewitness. And, because it’s who I am, I gave security tips too.
My cousin, who is an Iraq and Afghanistan soldier with all kinds of rank and medals, reached out to me via Facebook and said, “I think your situation was much worse than any Middle East situation.” Which I thought odd because he’s had his best buddy blown up right next to him. Then he said, “When I deploy I’m armed, geared up and expecting to fight. You were at a peaceful gathering around families and innocent civilians, not expecting bombs. That makes it much worse.”
“We accept the possibility of death and destruction when we sign our contracts. I’m sure no one who signed up for the marathon expected this.”
This completely messed me up, putting into perspective just how awful this situation is.
I only slept three hours that night, on edge, emotional and fragile. The next day, I headed to the media compound near Boylston to meet with Maria Menounos from Extra, who is a Boston girl. I connected with Maria, and within two minutes we were both crying. She started talking about how she loves Boston so much, then I started crying, then she started crying…which completely messed me up. I tell you this because she told me people should know this is real and they can’t forget. She was professional, but she was real. She put me at ease and we got through the interview.
Since then I’ve done more media on this than I wished, including the Boston Globe, Dr. Drew, Extra, Current TV, Canadian TV, again and again, Fox Boston and some radio.
In early May after the blasts, I was asked to speak to the North Eastern Massachusetts Law Enforcement Council on the benefits of social media to law enforcement and how social can help get the word out in a tragedy. When I walked into the room to speak, everyone was in uniform. What I didn’t know was many of the men and women attending were the first responders saving lives at the finish line, and others who were involved in the capture of the bombers.
That was a very emotional speech for me. Check out the Huffington Posts blog on how the Boston Police did a stellar job using Twitter during the bombing.
At this point, my family and I are safe, like most of America. Emotions are still high for some. We are sad and angry. Our hearts are heavy, knowing lives were lost, and that so many will never be the same. We are not at ease, and we all want answers. We wonder, sadly, whether this celebratory event will forever be marked by the visual of a plume of smoke that symbolized the evil intent of misguided people that do not value human life and have no regard for our freedoms.
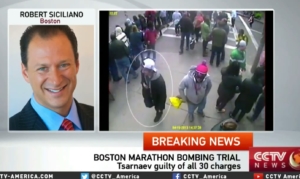 We caught the bastards and while there are no answers yet, and we may never get them. We must keep in mind the immediate needs of the victims and their families. On behalf of my Boston, we also must declare that we are proud of our city, its first responders and its people, who showed the true measure of the human spirit through powerful acts of kindness and displays of citizen courage. We are strong as a city, undivided as a country and unbowed by this attack. No terrorist will be allowed to alter our nation’s course.
We caught the bastards and while there are no answers yet, and we may never get them. We must keep in mind the immediate needs of the victims and their families. On behalf of my Boston, we also must declare that we are proud of our city, its first responders and its people, who showed the true measure of the human spirit through powerful acts of kindness and displays of citizen courage. We are strong as a city, undivided as a country and unbowed by this attack. No terrorist will be allowed to alter our nation’s course.
Please like my Facebook Page to stay in touch with my marathon progress, see you at the finish line!







 We caught the bastards and while there are no answers yet, and we may never get them. We must keep in mind the immediate needs of the victims and their families. On behalf of my Boston, we also must declare that we are proud of our city, its first responders and its people, who showed the true measure of the human spirit through powerful acts of kindness and displays of citizen courage. We are strong as a city, undivided as a country and unbowed by this attack. No terrorist will be allowed to alter our nation’s course.
We caught the bastards and while there are no answers yet, and we may never get them. We must keep in mind the immediate needs of the victims and their families. On behalf of my Boston, we also must declare that we are proud of our city, its first responders and its people, who showed the true measure of the human spirit through powerful acts of kindness and displays of citizen courage. We are strong as a city, undivided as a country and unbowed by this attack. No terrorist will be allowed to alter our nation’s course.























