How to Secure Your iCloud
By now you’ve heard that Jennifer Lawrence’s (and other celebs’) cellphone nude pictures were leaked out, but how in the heck did the hacker pull this off? Tech experts believe it was through the “Find My iPhone” app.
 Someone anonymously posted nude photos of Jennifer Lawrence and Kate Upton to the 4Chan site, and the stars confirmed the photos were of them.
Someone anonymously posted nude photos of Jennifer Lawrence and Kate Upton to the 4Chan site, and the stars confirmed the photos were of them.
It’s possible that the hacker/s discovered a vulnerability in the Find My iPhone service. This app helps people locate missing phones via cloud. hackers use a “brute force” program to protect hack accounts. These programs make repeated guesses at random passwords for a particular username until a hit is made.
So it’s possible hackers used “iBrute” to get celebs’ passwords, and hence, the photos in their iCloud accounts.
This is only a theory, as most hacking occurs in a more straightforward manner such as:
a person receiving a phishing email and responding with their password
someone’s personal computer gets hacked and spyware is installed
a laptop with all kinds of data is stolen
the wrong person finding a lost cellphone.
Also, evidence suggests that some of the leaked photos came from devices (like Android) that won’t back up to the iCloud.
Apple is investigating the leaks, and apparently put out a security upgrade Sept. 1, to prevent a brute force service from getting passwords via Find My iPhone.
You yourself are at risk of this breach if brute force indeed was used, as long as the problem hasn’t been fixed. If someone has your username, this tactic can be used.
If you want 100 percent protection, stay off the Internet. (Yeah, right.)
Bullet proof your passwords
- Each site/account should have a different password, no matter how many.
- Passwords should have at least eight characters and be a mix of upper and lower case letters, numbers and symbols that can’t be found in a dictionary.
- Use a password program such as secure password software.
- Make sure that any password software you use can be applied on all devices.
- A password manager will store tons of crazy and long passwords and uses a master password.
- Consider a second layer of protection such as Yubikey. Plug your flashdrive in; touch the button and it generates a one-time password for the day. Or enter a static password that’s stored on the second slot.
- Have a printout of the Yubikey password in case the Yubikey gets lost or stolen.
- An alternative to a password software program, though not as secure, is to keep passwords in an encrypted Excel, Word or PDF file. Give the file a name that would be of no interest to a hacker.
- The “key” method. Begin with a key of 5-6 characters (a capital letter, number and symbols). For example, “apple” can be @pp1E.
- Next add the year (2014) minus 5 at the end: @pp1E9.
- Every new year, change the password; next year it would be @pp1E10. To make this process even more secure, change the password more frequently, even every month. To make this less daunting, use a key again, like the first two letters of every new month can be inserted somewhere, so for March, it would be @pp1E9MA.
- To create additional passwords based on this plan, add two letters to the end that pertain to the site or account. For instance, @pp1E9fb is the Facebook password.
- Passwords become vulnerable when the internet is accessed over Wi-Fis (home, office, coffee shop, hotel, airport). Unsecured, unprotected and unencrypted connections can enable thieves to steal your personal information including usernames and passwords.
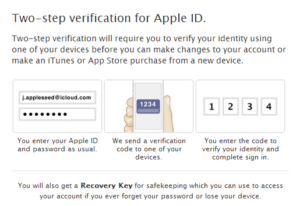
Use two-step verification.
Apple’s iCloud asks users two personal questions before allowing access. And let’s face it: We’re all wondering what Jennifer Lawrence was thinking when she decided it was a smart idea to put her nude photos into cyberspace.
Passwords seem to be the common thread in data breaches. But passwords aren’t too valuable to a hacker if they come with two-factor authentication. This is when the user must enter a unique code that only they know, and this code changes with every log-in. This would make it nearly impossible for a hacker to get in.
Go to applied.apple.com and you’ll see a blue box on the right: “Manage Your Apple ID.” Click this, then log in with your Apple ID. To the left is a link: “Passwords and Security.” Click that. Two security questions will come up; answer them so that a new section, “Manage Your Security Settings,” comes up. Click the “Get Started” link below it. Enter phone number and you’ll receive a code via text. If your phone isn’t available, you can set up a recovery key, which is a unique password.
All that being said, two factor will not protect your phones data. Apple is lax in making this happen. What Apples two factor does is protect you when you:
- Sign in to My Apple ID to manage your account
- Make an iTunes, App Store, or iBooks Store purchase from a new device
- Get Apple ID related support from Apple
Robert Siciliano is an identity theft expert to BestIDTheftCompanys.com discussing identity theft prevention. For Roberts FREE ebook text- SECURE Your@emailaddress -to 411247. Disclosures.